A cryptocurrency wallet maker said this week that hackers can break into Apple devices using the “zero-day” iMessage exploit, but all signs point to an exaggerated threat, if not outright fraud.
Trust Wallet has raised a panic
Trust Wallet’s official X account (formerly Twitter) wrote: “We have credible intel regarding a high-risk zero-day exploit targeting iMessage on the Dark Web. This can infiltrate your iPhone without clicking any link. High-value targets are likely. Each use raises detection risk.”
The wallet maker recommended that iPhone users disable iMessage completely “until Apple fixes this,” although there is no evidence that “this” even exists.
The tweet went viral and has been viewed more than 3.6 million times. Because of the attention the post garnered, Trust Wallet, which is owned by cryptocurrency exchange Binance, wrote a follow-up post a few hours later. The wallet maker doubled down on its decision to go public, stating that it is “proactively informing the community of any potential threats and risks.”
As it turns out, according to Trust Wallet CEO Eowyn Chen, the “information” is an advertisement on a darknet site called CodeBreach Lab, which offers a purported exploit for $2 million in the bitcoin cryptocurrency. The ad, titled “iMessage exploit,” claims that the vulnerability is a remote code execution (or RCE) exploit that requires no interaction with the target – commonly known as a “zero-click” exploit – and works in the latest version of iOS. Some bugs are called “zero days” because the vendor doesn’t have time or zero days to fix the vulnerability. In this case, there is initially no evidence that the exploit exists.
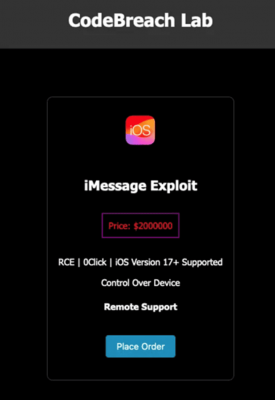
Screenshot of a dark web ad claiming to sell the alleged iMessage exploit. Photo provided by TechCrunch
What are the dangers of zero-day exploits
RCEs are some of the most powerful exploits because they allow hackers to remotely gain control of their target devices over the Internet. An exploit like RCE, coupled with the ability to zero-click, is incredibly valuable because these attacks can be carried out stealthily, without the knowledge of the device owner. In fact, a company that acquires and resells zero-day exploits is currently offering between $3 and $5 million dollars for these types of zero-day zero-click exploits, which is also a sign of how difficult it is to find and develop these types of exploits.
Given the circumstances of how and where this zero-day is being sold, it’s very likely that it’s all just a scam, and Trust Wallet fell for it by spreading what people in the cybersecurity industry would call FUD, or “fear of uncertainty and doubt.”
Zero-days do exist, and government hacking units have been using them for years. Users are advised to enable quarantine mode, a special mode that disables certain features of Apple devices in order to reduce the opportunities that hackers can use to attack iPhones and Macs. According to Apple, there is no evidence that anyone has successfully hacked anyone’s Apple device using quarantine mode.
TechCrunch checks
CodeBreach Lab is a new website with no experience. On its homepage – complete with typos – CodeBreach Lab claims to offer several types of exploits other than iMessage, but provides no further evidence.
The owners describe CodeBreach Lab as a “cyberattack nexus.” But it would probably be more accurate to call it a nexus of braggadocio and naiveté. An attempt to buy the alleged exploit by TechCrunch to verify the information yielded nothing. The website asked for the buyer’s name, email address, and then to send $2 million dollars in bitcoins to a specific wallet address on the public blockchain. Naturally, no one has done this yet.
Basically, if someone wants to get this alleged exploit, they have to send $2 million dollars to a wallet that belongs to an unknown person, all without contacting the owners of the website.

